
摘要
Summary
比特币是一个完全地点对点的改进版电子现金,将支持一方直接发送给另外一方的在线支付方式,而无需通过金融机构。“数字签名”提供了部分解决方案,但如果还是需要一个被信任的第三方来防止“双重支付”,则丧失了其关键价值。我们提出的“双重支付”问题解决方案是使用“点对点”网络。该网络使用“hashing(哈希)”将交易打上“时间戳”,以此将所有交易合并为一个不断延展的基于哈希的“工作量证明”链条,构成记录。除非重建“工作量证明”,该记录不可能被篡改。最长的链条不仅作为被目击事件序列的证明,还该证明来自最大规模的CPU算力池。只要被节点所控制的大多数CPU算力没有协同一致攻击网络,那么他们将生成最长的链条,超越攻击者。此网络本身只需极少的基础设施。信息尽最大努力进行广播,节点可以随意离开或重新加入网络,其离线期间所发生,由其接收最长的“工作量证明”链条即可验证。
Bitcoin, a fully site-to-place improved electronic cash, will support one party's direct online payment to another, without the need to pass through financial institutions. “Digital signature” offers a partial solution, but if a trusted third party is still needed to prevent “double payment”, it loses its key value. The solution we propose for “double payment” is to use a “point-to-point” network. The network uses “hashing (Hashi)” as a “time stamp” on transactions, thus combining all transactions into an ever-expanding Hashi-based “ workload proof” chain that constitutes a record. Unless the “volume proof” is reconstructed, the record cannot be tampered.

一、导言
i. Introduction
互联网商业,逐渐发展成为几乎完全借助作为被信任第三方的金融机构来处理电子支付业务。然而,该系统即使目前运转良好,足以应付大多数交易业务,但它还是受困于其固有的“基于信任模式”缺陷的问题。“完全不可逆交易”并非真正可行,原因是会导致金融机构不能避免地卷入争端的调解。这种调解成本导致的交易成本增加,限制了可实现交易的最小规模,同时断绝了日常小额交易的可能性,而且还有一种更为广义的成本,即为不可逆服务而设计出来的不可逆支付能力将会减弱。伴随着撤销可能性的是信任需求扩张。商人们必须对他们的顾客保持戒备,由此,为了获取更多的信息不断烦扰顾客,远超他们所需。甚至无可奈何地接受一定程度上的欺诈。,人们使用物理货币时,这些成本与支付的不确定能够避免,但,没有商家会通过一种没有信任方的信息渠道进行支付。
Internet commerce, which evolves almost exclusively to deal with electronic payments through financial institutions that are trusted as third parties. However, even if the system is functioning well enough to deal with most transactions, it still suffers from its inherent “trust-based” defects. “Absolutely irreversible transactions” are not really feasible because financial institutions cannot avoid being involved in dispute mediation. The transaction costs of such mediation limit the possibility of making transactions small enough to materialize, while cutting off the possibility of day-to-day small transactions, and there is a broader cost, namely, that the irreversible capacity to pay, designed for irreversible services, will be reduced.
因此,一种以建立在密码学基础上的证明来替代信任的电子支付系统,就很有必要,该系统允许任何有交易意愿的双方直接相互交易,而不需要一个被信任的第三方。在计算上不可能撤销的交易将保护卖方不被,常规的第三方中间商亦能够轻松地实现对买方的保护。这篇论文里,我们提出一种双重支付问题解决方案,就是使用一种点对点分布式时间戳服务器,以生成可计算的、按时间的前后顺序排列的交易序列证明。只要诚实的节点共同控制的CPU算力,比协同操作的攻击者节点集团更多,这个系统就是安全的。
Thus, an electronic payment system that replaces trust with a cryptographic-based certificate is necessary to allow any willing parties to deal directly with each other without the need for a trusted third party. Transactions that cannot be calculated to be avoided will protect the seller from being denied, and conventional third-party intermediaries will be able to easily protect the buyer. In this paper, we propose a solution to the problem of double payment by using a point-to-point time stamp server to generate quantifiable evidence of sequences of transactions in chronological order of time. The system is safe as long as honest nodes jointly control CPUs more than coordinated attacker nodes groups.
艾瑞咨询:数字货币通过第三方支付兑换流通已有政策铺垫:艾瑞咨询今日发布《2020中国第三方跨境支付行业研究报告》,其中指出数字货币推广和第三方支付应用是相辅相成而非相互替代的关系,因为今年发布的《非银行支付机构客户备付金存管办法》已经规定非银行支付机构按规定通过现金形式为客户办理备付金赎回的,应当先通过备案自有资金账户办理,再通过备付金主监督机构从备付金集中存管账户将相应额度的客户备付金划转至备案自有资金账户,这一规定对应的业务场景正是用户将目前的第三方数字钱包账户余额兑换为数字货币应用,因此数字货币通过第三方支付兑换流通已有政策铺垫。[2021/8/14 1:54:11]
Eri Consulting: A policy advance has been made for digital currency flows through third-party payments: A study of the Chinese third-party cross-border payment industry for 2020 was issued today by Erie Consulting, which noted that the promotion of digital currency and third-party payment applications are complementary rather than substitute relationships, since the Measures for the Custody of Payments by Clients of Non-Bank Payments Agencies, issued this year, already requires non-bank payment agencies to make deposits for customers in the form of cash as required, should be processed by filing their own funds accounts and then transfer the corresponding amount of the customer's payment from the central deposit management account through reserve monitoring agencies to filing their own funds accounts, and that the corresponding business scene is where the user converts the balance of the current third-party digital wallet account into a digital currency application, so that the digital currency, through third-party convertibles, has a policy in place. [2021/8/14:54:11]

二、交易
II. Transactions
我们规定电子货币等同于数字签名链。每一位所有者转移其电子货币给下一位,通过数字签署一个哈希,这个哈希是前一个交易的,和下一个所有者的公钥,和加在电子货币的末端。收款人能够通过核对签名来证明该链所有权。
We provide that the electronic currency is equivalent to the digital signature chain. Each owner transfers its electronic currency to the next, signs a Hashi by number, which is the previous transaction and the next owner’s public key, and adds it to the end of the electronic currency. The payee can prove ownership of the chain by checking the signature.
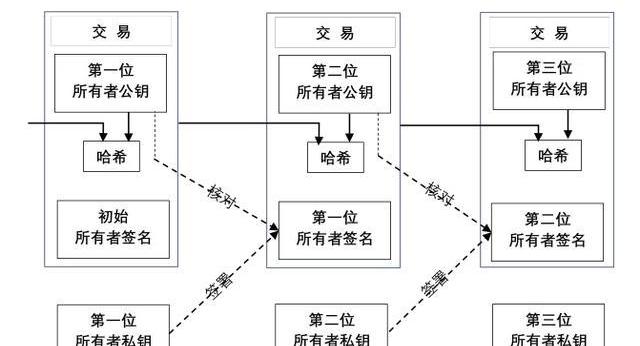
问题当然就是收款人不能核实某个所有者没有“双重支付”该币。普通的解决方案是引入一个被信任的中心权威,或铸币厂,以核对每一笔交易是否双重支付。每笔交易完成后,货币必须回收到铸币厂以发行新币,而且仅铸币厂发行的货币能够被信任不会“双重支付”。此方案的问题是整个货币系统的命运依赖于公司来运行铸币厂,导致每一笔交易不得不通过他们,就好象一家银行。我们需要一种方式,来帮助收款人知晓前任所有者没有签署任何更早的交易。为了我们的目的,最早的一笔交易是重要的,这样我们不必担心后来者试图“双重支付”。证实一笔交易是否存在的唯一方式,就是使得所有的交易都是可知的。在基于铸币厂的模式里,铸币厂是所有交易的知情者,而且清楚哪一笔最先到达。没有一个被信任方情况下,要达到这一点,交易必须公开广播,如此,则我们需要一个系统,该系统可使参与者对他们接收到顺序的单一历史达成共识。收款人需要证明每一笔交易的时点,大多数节点承认该交易为最先被接收的交易。
The problem is, of course, that the payee cannot verify that a certain owner does not have “double payment” of the currency. The common solution is to introduce a central authority that is trusted, or a casting factory, to check whether each transaction is double-payment. For our purposes, the first transaction is important, so we do not have to worry about subsequent attempts to “double-payment.” The only way to verify that a transaction exists is to make all transactions known. In a model based on a molar, the molar is the informed owner of all transactions, and it is clear which of the first transactions has to come through, as if they were one. In the absence of a trusted party, the transaction has to be publicly broadcast, so we need a system that allows participants to reach a common understanding of their order.
三、时间戳服务器
iii, time stamp server
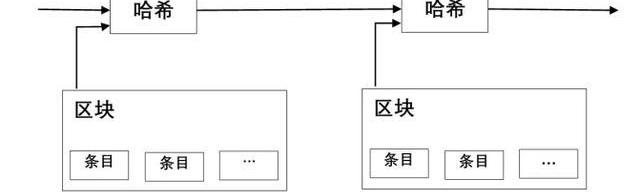
我们提出的解决方案始于一种时间戳服务器。时间戳服务器通过从被时间戳记的项目区块中提取哈希并广泛地传播该哈希来运转,类似在报纸上或在全球新闻网络发邮件。该时间戳验证数据在某一时点确实存在,显然,目的是加入到哈希中。每一个时间戳都包括前一个被加入到哈希中的时间戳,形成一个链条,因为每一条追加的时间戳补充其前一个时间戳。
The solution we are proposing starts with a time stamp server. The time stamp server operates by extracting Hashi from a project block that is time-stamped and spreading it widely, similar to emailing in newspapers or on the global news network. The time stamp validation data do exist at a certain point in time, apparently with the aim of joining Hashi. Each time stamp includes the first one that was added to Hashi, forming a chain, because each additional time stamp complements the previous one.
声音 | Altmarket CEO:数字货币经济进入了第一个衰退期:Altmarket的CEO Bryce Weiner在Twitter发文表示,数字密货币经济目前已经经历了整整四分之一的负增长。我们已经进入了第一个衰退期。[2018/11/25]
Altmarket CEO: The digital currency economy has entered its first recession: CEO Bryce Weiner of Altmarket wrote on Twitter that the digital currency economy has now experienced a full quarter of negative growth. We are already in our first recession. [2018/11/25]
四、工作量证明
iv. Certification of workload
要在点对点的基础上构建一个分布式时间戳服务器,我们将需要用到与亚当贝克创造的“哈希现金”类似的“工作量证明”系统,而不是报纸或全球新闻网络邮件。在进行哈希计算时,该“工作量证明”引入对于某一个值的检索工作,比如运行SHA-256,该哈希值从某一数量的0字符开始。其所需的平均工作量是所需0字符数量的指数,而则能通过仅仅执行一次哈希计算来检验。对于我们的时间戳网络,我们在区块中某一随机数,给定的区块哈希值所需的零字符串,直到找到一个值为止,以构建“工作量证明”机制。只要CPU算力被消耗在满足“工作量证明”机制上,则区块不能被修改,除非重新进行工作。由于下一区块链接其后,修改区块的工作量必须包括重建其后面的所有区块。
For a distributed time stamp server to be constructed on a point-to-point basis, we would need to use a “ workload certificate” system similar to the “Hashi cash” created by Adam Baker, rather than a newspaper or global news network mail. In the Hashi calculation, the “volume certificate” introduces a search for a particular value, such as running the SHA-256, which starts with a certain number of zero characters. The average amount of work required is an index of the number of 0 characters required, which can be tested by simply performing a Hashi calculation. For our time stamp network, we give a random number of zero strings in a given block of Hashi value until a value is found to construct a “ workload proof” mechanism. As long as the CPU calculation is consumed to satisfy the “volume proof” mechanism, the block cannot be modified unless it is re-worked. For the next link, the workload of modifying the block must include rebuilding all the blocks behind it.
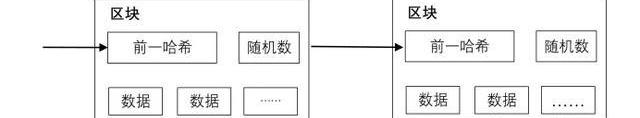
“工作量证明”机制也解决了代理作出大多数判断的人选确定问题。如果该“大多数”建立在“一个IP地址一张选票”的基础上,它将被破坏,因为每一个人都能够分配到很多IP。“工作量证明”实质上是“一个CPU一张选票”。最长的链条代表大多数判断,因为该链条拥有尝试投入进来的最大量“工作量证明”。如果CPU算力的大多数由诚实的节点控制,诚实的链条将以超过其他与之竞争链条的速度快速生长。为改变一个已完成区块,一个攻击者将被迫重建区块“工作量证明”,以及所有后接区块,然后追上,超过诚实节点的工作量。我们稍后将提及,由于随后区块持续增加,一个稍慢的攻击者追上的概率以指数级减少。随着时间的推移,计算机硬件速度的持续加快和运行节点的兴趣变化无常,为了应对上述情况,“工作量证明”机制的难度通过一种以设定每一小时产生区块的平均数量为目标的动态平均来调节,如果增长太快,难度将增加。
The “volume proof” mechanism also solves the problem of identifying agents who make most of the judgement. If the “most” is based on a “one IP address with a vote”, it will be destroyed because everyone can distribute many IPs. The “volume proof” is essentially “one CPU with a vote. The longest chain represents most of the judgement because it has the largest amount of “volume proof” that attempts to invest. If the majority of CPU computing power are controlled by honest nodes, the honest chain will grow faster than other competing nodes. In order to change a completed block, an attacker will be forced to rebuild the block “volume proof” and all subsequent nodes, and then catch up with more than the honest node. We will mention later that the probability of a slower attacker following the node is reduced at the exponential level as a result of the continuous increase in the number of blocks that follows.
五、网络
V, Web
运行网络的步骤如下所示:
The steps to run the network are as follows:
动态 | 欧洲大型交易所基金Flow Traders NV进军数字货币市场:据彭博报道,欧洲大型交易所基金Flow Traders NVI日前进军数字货币市场。位于荷兰的Flow Traders NV正基于比特币和以太坊为基础,创建首批交易所交易票据。[2018/7/6]
Flow Trades NV, a major European exchange fund, has moved into the digital currency market: according to Bloomberg, the European large exchange fund Flow Trades NV is moving forward in the digital currency market. The Dutch-based Flow Traders NV is creating the first exchange trading instruments based on Bitcoins and Taiku.[2018/7/6]
1)新的交易向所有的节点广播。
1) New transactions are broadcast to all nodes.
2)每一个节点将新的交易纳入一个区块。
2) Each node integrates a new transaction into a block.
3)每一个节点努力为自己区块寻找一个具有一定难度的“工作量证明”。
3) Each node tries to find a difficult “workload certificate” for its own block.
4)当一个节点找到了“工作量证明”,它向所有节点广播该区块。
4) When a node is found, it broadcasts the block to all nodes.
5)当且仅当区块里面的所有交易有效且之前从未发生时,节点才接受该区块。
5) When and only when all transactions in a block are valid and have never occurred before, the node is accepted.
6)节点通过追加链条中的下一区块的工作以表示其对区块的接受,使用该被接受区块的哈希作为前置哈希。
6) Node expresses its acceptance of the block by adding the next block in the chain, using as a pre-Hashi the accepted block.
节点总是把最长的链条视为正确,并将持续延长该链条。如果两个节点在同一时点广播的下一区块描述并不一致,一些节点会率先接受其中一个或另一个区块。在此情况下,他们工作于率先被他们接受的区块,但保存另外分叉以防其变得更长。当下一个“工作量证明”被找到,以及一个分叉变得更长时,这种“平局”将被打破;工作在其他分叉上的节点最后将转到这个较长的区块。
Nodes always see the longest chain as correct and will continue to extend the chain. If the next block of the two nodes broadcast at the same time is not described in the same time, some nodes will take the lead in accepting one or the other. In this case, they work to take the first block they accept, but save another fork to prevent it from becoming longer. When the next “worker certificate” is found, and a split becomes longer, the tie will be broken; the nodes on the other nodes of the work will eventually be transferred to this longer block.
新交易的广播并非一定需要到达所有的节点。只要他们到达多数节点,他们将在短时间内被纳入一个区块。区块广播亦对缺失的信息具有容错功能。如果一个节点没有收到某个区块,它将在接收下一区块,且意识到缺失了一个区块时,提出请求。
When they reach most nodes, they will be included in a block within a short period of time. Blocks also have the ability to accommodate missing information. If a node does not receive a block, it will make a request when it receives the next block and is aware that a block is missing.

六、激励机制
vi. Incentives
根据规则,区块里的第一笔交易是一笔特殊交易,该交易产生一枚归属于区块创造者的新币。这将增加节点支持网络的激励,并且提供一种方式来开始货币分配并进入流通,因此这是一种没有中心机构的发行方式。这种新货币数额持续稳定的增长类似于黄金矿工耗费资源来增加黄金流通。.就我们来说,这类资源就是被耗费CPU时间和电力。
According to the rules, the first deal in the block is a special deal, which generates a new currency that belongs to the creator of the block. This will increase incentives for node support networks, and provide a way to start the distribution and circulation of money, which is therefore a way of issuing without a central institution.
此类激励亦可见于交易费用。如果一笔交易的输出值低于其输入值,其差额就是交易费,用以增加控制交易区块的激励价值。一旦一个预先设定的货币数量已经进入流通,该激励则全部转变为以交易费用,并可完全地免除通货膨胀。
If the output value of a transaction is below its input value, the difference is the transaction fee, which increases the incentive value of the control block. Once a predefined amount of money is in circulation, the incentive is converted into a transaction cost and completely free of inflation.
24小时数字货币行情梳理:根据Bitfinex交易平台数据显示,
A 24-hour digital monetization: According to data from the Bitfinex trading platform,
BTC最新成交价格53682.8元,最高价达55204.04元,最低价格53283.65元,成交量1.98万,涨幅0.39%;
(a) The latest BTC transaction price of $53,682.8 with a maximum price of $55,204.04 and a minimum price of $53,283.65, with a turnover of 198,000 and an increase of 0.39 per cent;
ETH最新成交价格4477.63元,最高价达4615.08元,最低价格4443.53元,成交量9.68万,跌幅1.71%;
(a) The latest ETH transaction price of $4477.63, with a maximum price of $4615.08, with a minimum price of $4443.53, with a turnover of $96,800 and a decline of 1.71 per cent;
BCH最新成交价格7820.79元,最高价达8382.79元,最低价格7746.7元,成交量3.52万,涨幅0.82%。[2018/5/22]
The latest BCH transaction price was $7820.79, with a maximum price of $8382.79, with a minimum price of $7746.7 and a volume of $35.2 million, with an increase of 0.82 per cent.[2018/5/22]
该激励还能有助于促使节点保持诚实。如果一个贪婪的攻击者有能力比诚实节点组织更多CPU算力,他将被迫进行选择,是通过欺诈以偷回其支付的款项,还是通过生成的新货币。他应当会发现,按照规则行事更加有利可图,这样的规则有利于他比其他联合起来的每一个人获取更多的新货币,亦优于破坏系统以及损害自己拥有财富的有效性。
If a greedy attacker is capable of organizing CPUs more effectively than an honest node, he will be forced to choose whether to steal the money he has paid by fraud or by generating a new currency. He should find that it is more profitable to act in accordance with the rules that make it easier for him to acquire more new money than everyone else who unites, and better to destroy the system and undermine the effectiveness of his own wealth.
七、恢复磁盘空间
vii. Resume disk space
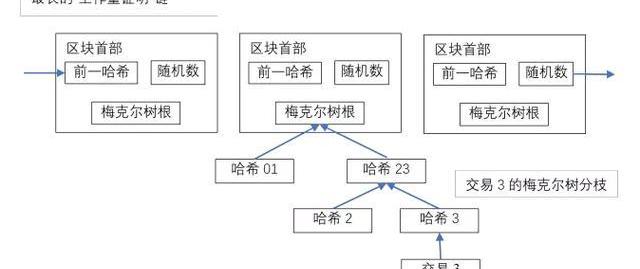
一旦一枚货币中的最后一笔交易被纳入了足够多的区块中,则能丢弃之前那些失效的交易以节省磁盘空间。为确保同时不破坏区块哈希,交易被随机散列在一棵“梅克尔树”上,仅仅将其“根节点”置入该区块哈希中。只需剪除此树的其他分枝,先前的区块则能够被压缩。内置的哈希无需保存。
Once the last deal in a currency is included in a sufficient number of blocks, it saves disk space by discarding previously invalid transactions. To ensure that the deal is not destroyed at the same time, the transaction is randomly scattered over a “Mekel tree” and simply places its “root” in that block. Just cut off the other branches of the tree, and the previous blocks can be compressed.
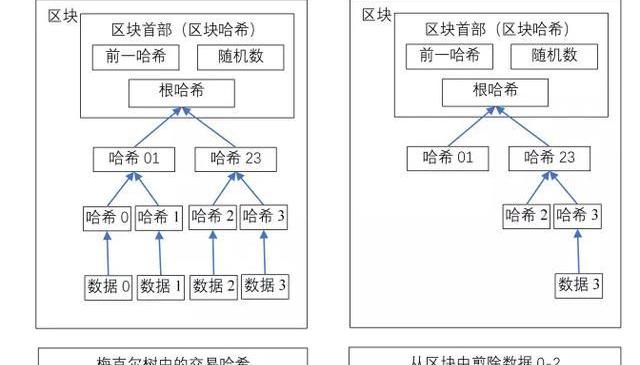
一个不含交易的区块首部大约是80字节。如果你希望在每10分钟左右生成一个区块,则每年约4.2MB(80B×6×24×365=4.2MB)。鉴于计算机系统在2008年通常以随机附带2GB存贮空间出售,而且摩尔定律预示现在的增长速度是1.2GB每年,则即使区块首部必须永久保存,存贮亦不成问题。
If you want to generate a block every 10 minutes or so, about 4.2 MB per year (80Bx6x24x365=4.2MB) is sold in 2008 with a random 2GB storage space. Given that Moor’s law predicts that the growth rate is now 1.2GB per year, storage will not be a problem even if the first block must be permanently preserved.
在不运行覆盖全网全部节点情况下,支付验证也是可能的。用户仅需保留一个最长“工作量证明”链条的区块首部备份,由此,他能够通过质询网络中节点,直到他确信拥有最长的区块链,从而达到通过“梅克尔树”分支将交易连接到被打上了时间戳的区块的目的。他无法自行检查交易,但通过连接到链条的某一位置,他能够看到一个网络节点已经接受了该笔交易,而且,在之后的追加区块,进一步证实了这个网络已经接受了该笔交易。
Payment certification is also possible in the absence of running all the nodes of the network. The user only needs to keep a first backup of the longest “ workload proof” chain, so that he can question the node in the network until he is convinced that he has the longest block chain and thus achieves the purpose of connecting the transaction through the Merkel branch to a block that has been time-stamped. He cannot check the transaction on his own, but by connecting to a point in the chain, he can see that a node in the network has already accepted the transaction, and the subsequent addition of blocks further confirms that the network has accepted the transaction.
八、简化的支付验证
VIII, Simplified payment certification
俄罗斯联邦金融监测局已经出面反对俄罗斯境内进行交易数字货币:据俄罗斯媒体Bits.media报道,俄罗斯联邦金融监测局(Rosfinmonitoring)已经出面反对俄罗斯境内进行交易数字货币。俄罗斯联邦金融监测局副主席Pavel Livandy在俄罗斯银行协会(ARB)的大会上发言表示,数字货币是高风险的投机资产,并没有真正的价值。3月初,俄罗斯金融市场委员会负责人提交了一份名为“数字金融资产”的法案草案,要求数字货币交易只能通过交换服务运营商进行数字资产交易。该委员会希望这种方法能够防止企图和其他金融动机的欺诈活动,交易所必须是在俄罗斯经营的合法实体。[2018/4/5]
The Financial Monitoring Service of the Russian Federation has spoken out against trading in digital currency in Russia: according to the Russian media Bits.media, the Russian Federation Financial Monitoring Service (Rosfinmonitoring) has spoken out against trading in digital currency in Russia. Pavel Livandy, Vice-President of the Financial Monitoring Agency of the Russian Federation, addressed the General Assembly of the Russian Banking Association (ARB), stating that digital currency is a high-risk speculative asset and has no real value. In early March, the head of the Russian Financial Markets Commission submitted a draft bill entitled “Digital financial assets” requiring digital currency transactions to be carried out only through the exchange of service operators. The Commission hoped that this approach would prevent attempted and other financial-motivated fraudulent activities, and that the exchange must be a legitimate entity operating in Russia.[2018/4/5]
此时,只要诚实节点控制网络,则验证是可靠的,但是,如果该网络被攻击者压服,则非常容易遭受攻击。虽然网络节点能够自己验证其交易,只要该攻击者能够继续压制该网络,简易方法将被攻击者伪造的交易所愚弄。必须采取一种针对性保护策略,以接收当网络节点发现无效区块时发出的报警信号,并提示用户软件下载整个区块及被报警交易,以确认其不一致。出于更加自主的安全保障和更快的验证考虑,接受大量日常频繁支付的商业机构很可能仍然希望运行他们自己的节点。
At this point, as long as an honest node controls the network, the test is reliable, but if the network is pressured by the attacker, it is very vulnerable to attack. While the node can verify its transaction itself, as long as the attacker can continue to suppress the network, the easy method will be fooled by the exchange that the attacker has forged. A targeted protection strategy must be adopted to receive the warning signals that are sent when the node discovers an invalid block and to alert the user to download the entire block and to be called to the transaction in order to confirm its inconsistency. For reasons of more autonomous security and faster certification, commercial agencies that receive a large number of frequent daily payments are likely still willing to run their own nodes.
九、价值的合并与分割
ix. Merger and division of values
尽管处理单个货币是可以的,但为了一次转让中的每一个货币而将一笔交易分割开来,将会变得很不便利。为允许价值进行分割和合并,交易包括多次输入及输出。通常地,要么是一个来自前一笔更大交易的单一输入,要么是合并了更小金额的多次输入,输出则至多只有两笔:一笔用来支付;另一笔找零。
While it is possible to deal with a single currency, it would be difficult to separate a transaction for each currency in a single transfer. To allow the value to be split and consolidated, the transaction consists of multiple input and output. Normally, either a single input from the previous larger transaction or a multiple input from a smaller amount is combined, with a maximum of two outputs: one for payment; and the other for zeroing.
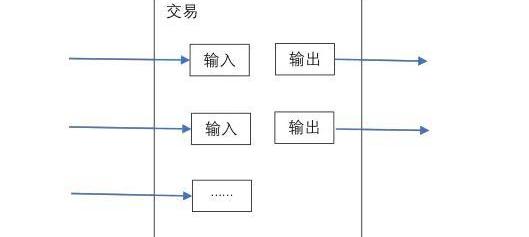
这时需要注意的是输出端,那里一笔交易依赖于多个交易,这些多个交易又依赖于更多的交易,这并无问题。从来不需要提取一个完全独立的交易历史备份。
What needs to be noted at this point is the export end, where a transaction depends on multiple transactions, which depend on more transactions, which is no problem. There is never a need to extract a complete stand-alone historical backup of the transaction.
十、隐私
10, privacy
传统的银行业务模式通过限制关联方获取数据入口和被信任的第三方来构建隐私等级。公开广播所有交易的必要性阻碍了这种方法施行,但是隐私还是可以通过在其他地方隔断信息流来保证:使用匿名持有的公钥。公众可以看见某人支付某金额给另外一人,但没有信息将此交易连接到任何人。这与股票交易所发布信息的方式类似,那里个人交易的时间和规模,即“报价”,是公开的,但不会告诉谁是交易方。
The traditional banking model builds privacy levels by limiting access to data by related parties and trusted third parties. The need for public broadcasting of all transactions hinders this approach, but privacy can still be guaranteed by blocking the flow of information elsewhere: using an anonymously held public key. The public can see someone paying a certain amount to another person, but there is no information to connect the transaction to anyone. This is similar to the way stock exchanges publish information, where the time and scale of individual transactions, i.e. the “price offer”, is public, but does not tell the parties to the transaction.
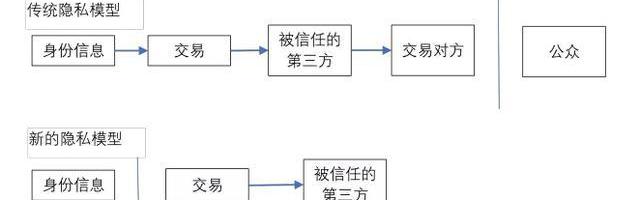
作为一个补充防火墙,一对新的钥匙被用于每一笔交易,以阻止他们连接到一个普通的所有者。有些连接还是不可避免,原因是多次输入的交易,必然会泄露出他们的输入来自相同的所有者。真正的危险是如果所有者的私钥被泄露,连接将会泄露属于此同一所有者的其他交易。
As a supplementary firewall, a new pair of keys is used in every transaction to prevent them from connecting to an ordinary owner. Some connections are inevitable, because multiple entries inevitably reveal the same owner's input. The real danger is that if the owner's private key is leaked, the connection will reveal other transactions belonging to the same owner.
十一、计算
11, Calculating
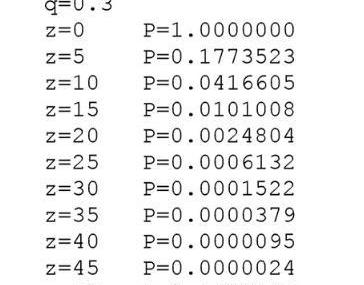
我们设想一个场景:一个攻击者试图比诚实链条更快地生成一个替代链条。即使其技术高超,还是无法做到突然侵入系统随心所欲地篡改,诸如无中生有地创造价值或者掠夺从未归属于他的财富等。节点将不会接受一笔无效的交易作为支付,而且,诚实的节点亦将不接受包含该无效交易的区块。一位攻击者仅能试图篡改一个他自己的交易,以收回最近消费的金钱。诚实链条和攻击者链条之间的竞赛可以描述为“二叉树随机漫步”。成功事件为诚实链条延展一个区块,则增加领先,是为“+1”;失败事件则是攻击者的链条延展一个区块,则缩减差距,是为“-1”。攻击者从一笔给定的亏损迎头赶上的概率与“徒破产问题”类似。假设一个徒,拥有无限透支信用,从一笔亏损开始,可以进行无限次数的测试以试图达到盈亏平衡点。我们能够计算他可能达到盈亏平衡点,或者攻击者赶上诚实链条的概率,如下所示:
We envisage a scenario in which an attacker tries to create an alternative chain faster than an honest chain. Even if it is technologically superior, it does not allow sudden intrusion into the system to be tampered with as it pleases, such as the uninhabited creation of value or looting of wealth that has never been attributed to him. Nodes will not accept an invalid transaction as payment, and honest nodes will not accept a block containing the invalid transaction. An attacker can only attempt to alter his own transaction to recover the money recently consumed. The race between the honest chain and the attacker's chain can be described as a “random of the two fork”; successful events extend a block of the honest chain to “+1”; failure is an extension of the chain of the attacker to “1”; failure is a reduction of the gap to “1”; the attacker's probability of catching up from a given deficit head is similar to that of “insolent insolvency”, assuming that there is a trail of credit, starting with a loss, and an endless test can be made to try to achieve a deficit balance.
p=诚实节点找到下一区块的概率
p = Probability of an honest node to find the next block
q=攻击者找到下一区块的概率
q= probability that the attacker will find the next block
qz=攻击者在Z区块后赶上的概率
qz = probability that the attacker will catch up with block Z
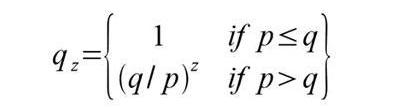
我们给定一个假设,p>q,随着攻击者不得不赶上的区块数量不断增长,其概率呈指数级下降。由于胜算与其相悖,如果他无法幸运地在早期取得突飞猛进,则将被远远地甩在后面,他篡改将变得微乎其微。我们现在考虑在充分确定付款人不能修改交易之前,此笔新交易的收款人需要等待多长时间。我们假设这位付款人是攻击者,他想让收款人相信当时已经支付了,过一段时间后,将其改换为支付给他自己。事情发生时,会惊动收款人,但这个付款人希望是为时已晚。收款人生成一对新的密钥,将公钥给予付款人,并在签署前预留较短时间。如此将阻止发生:付款人通过连续不断地工作,提前准备区块链,直到他非常幸运地到达足够远的前方,,然后执行该交易。一旦该交易发送,不诚实的付款人在一条包含一项他的交易替代版本的并行的链条上秘密开始工作。收款人等到该笔交易已经纳入了一个区块,且已有Z个区块连接在后。他并不知道攻击者已经制造增长的确切数量,但假设诚实区块在每一区块上预期耗费的时间的均等,攻击者区块潜在增长将呈“泊松分布”,期望值为:
We now consider how long it will take for the payer of the new transaction to wait until it is fully determined that the payer cannot modify the transaction. We assume that the payee is the attacker, who wants him to believe that the payment was made and, after a certain period of time, changed to his own. The payee will be shocked when it happens, but the payee hopes that it will be too late. The payee will generate a new key, give the payee the public key, and leave it for a short period of time before signing the deal: the payer will work through continuous work, prepare the chain well in advance, until he is very fortunate enough to reach the front, and then execute the transaction. Once the payee is sent, the payer will hope is too late.
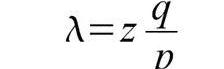
为了获取攻击者追赶上的概率,我们将攻击者取得进展区块数量的泊松分布的概率密度,与在该数量下攻击者依然能够追赶上的概率相乘:
In order to obtain the probability that the attacker will catch up, we multiply the probability density of the distribution of the number of blocks in which the attacker will make progress by multiplying the probability that the attacker will still be able to catch up with that number:
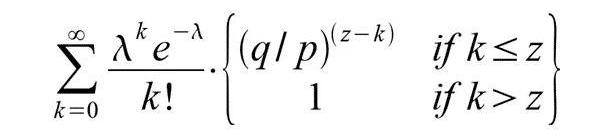
转换为以下形式,以避免无穷数列求和……
Convert to the following form to avoid endless numbers of claims...
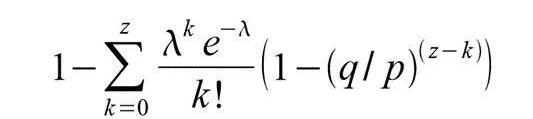
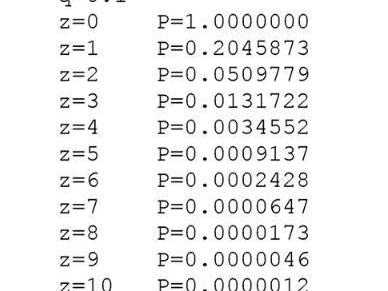
转换为C语言代码……
Converts to C-language code...

运行结果,我们能够看到概率Z值呈指数级下降。求解,令P少于0.1%时的Z值……
Run results, we can see the probability Z is down exponentially. To solve the problem, P is below the Z value of 0.1%.
十二、结论
12, conclusions
我们提出一个无需借助信任的电子交易系统。我们一开始,基于数字签名生成货币的普通框架,提供强有力的所有权控制,但无法完全防止“双重支付”。为解决此问题,我们提出一种点对点网络,运用“工作量证明”来记录一个公共的交易历史,对攻击者来说,如果大多数CPU算力由诚实节点控制的,则篡改很快变成在计算上是不可实现的。该网络因其简单随意的拓扑结构而粗壮皮实。节点只需很少的协调即可协同工作。他们无需辨认,因为信息无需路由到某些特定区域,仅需尽最大努力传播即可。节点能够随时离开和重新接入网络,其离线期间所发生所有交易,由其接收“工作量证明”链条即可验证。他们以CPU算力投票,并以努力延展有效区块和拒绝在无效区块后延展方式来表达他们的意见,即是否接受某区块的意见。通过这种共识机制,任何必需的规则和激励都能够被强制执行。
In order to address this problem, we propose a network of point-to-points, using “volume certificates” to record the history of a public transaction, and for the attackers, if most CPU computing is controlled by honest nodes, it will quickly become unattainable in calculations. The network is co-ordinated by its simple and random puncture structure. The nodes need little coordination to work together. They need no recognition, because the information needs no route to particular areas, and they need to do their best to disseminate it. The nodes can leave and re-enter the network at any time, and all transactions that occur during their absence can be verified by receiving the CPU chain. They vote in terms of the CPU, and they can express their views in a way that seeks to extend the effective blocks and refuses to extend them after the invalid ones. Through this mechanism of consensus, any rules and incentives that are needed can be enforced.
参考文献
References
W.Dai,《B币》,http://www.weidai.com/bmoney.txt,1998年。
W. Dai, Currency B, http://www.weidai.com/bMoney.txt, 1998.
H.Massias,X.S.Avila,andJ.-J.Quisquater,《只需最小信任的安全时间戳服务器设计》,比荷卢经济联盟第二十届信息理论学术报告会,1999年5月。
Massias, X.S. Avila, and J.-J. Quisquater, “Designation of a server with minimal trust security time”, Twentieth Scientific Report on Information Theory, Béholux Economic Union, May 1999.
S.Haber,W.S.Stornetta,《如何对数字文件进行时间戳记录》,《密码学期刊》,1991年第2期,第99-111页。
S. Haber, W.S. Storneta, How to Stall Digital Documents in Time, The Journal of cryptography, No. 2, 1991, pp. 99-111.
D.Bayer(拜尔),S.Haber,W.S.Stornetta,《提升数字时间戳的效率和可靠性》,《序列二:通讯安全及计算机科学之理论》,第329-334页。
D. Bayer (Bail), S. Haber, W. S. Storneta, “Enhancing the efficiency and reliability of digital time stampes”, Series II: Theory of Communications Security and Computer Science, pp. 329-334.
S.Haber,W.S.Stornetta,《字符串安全命名》,国际计算机学会第四届年会关于计算机和通讯安全的会议记录,第28-35页,1997年4月。
S. Haber, W.S. Storneta, String Safety Naming, Proceedings of the Fourth Annual Conference of the International Computer Society on Computer and Communication Security, pp. 28-35, April 1997.
A.Back,《哈希现金——拒绝服务攻击之反制方案》,http://www.hashcash.org/papers/hashcash.pdf,2002年。
A. Back, Hashi Cash — Reverse Program to Reject Service Attacks, http://www.hashcash.org/papers/hashcash.pdf.
R.C.Mekle,《公钥密码系统协议》,电子与电气工程师学会,1980年安全与隐私学术报告会会报,第122-133页,1980年4月。
R.C. Meckle, Public Key Password System Agreement, Society of Electronics and Electrical Engineers, Security and Privacy Academic Report 1980, pp. 122-133, April 1980.
W.Feller,《概率论及其应用介绍》。
W. Feller, Introduction to Probability and its Application.
标签:CPU区块链HCAACK门罗币cpu算力表区块链技术通俗讲解无中介dashcashCryptojacks
Label: CPUhttps://ahref=https://www.qjnu.com/tag/HCA.html" HCA
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群



















发表评论